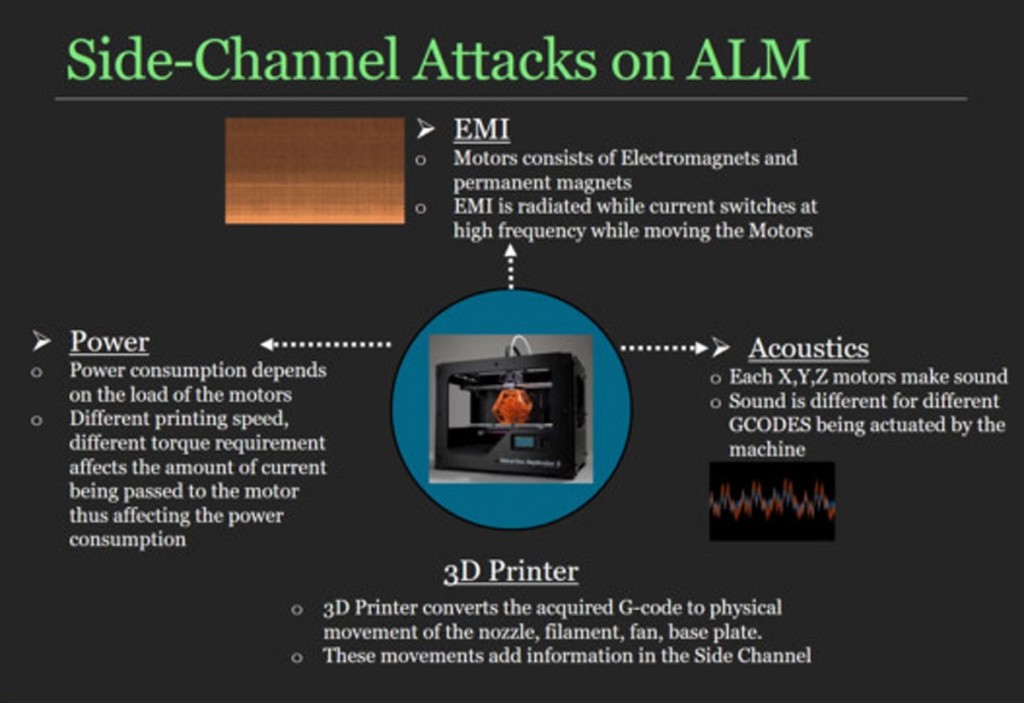
On 3DPI, we’ve covered numerous stories of IP theft and IP protection services. Typically, the biggest concern for interested parties is the loss of valuable CAD files online. After all, torrent sites have allowed users to download the complete Phil Collins discography in minutes, who’s to say that the files for 3D printing an engineer’s important prototype wouldn’t end up online, as well? Most solutions to this problem involve streaming files directly to a 3D printer, so that none of the models actually pass through the hands of those doing the printing. However, a new study from University of California, Irvine demonstrates that this may not be enough. 3D designs may also be stolen via the sound of the printer itself.
The research, led by director of UCI’s Advanced Integrated Cyber-Physical Systems Lab Mohammad Al Faruque, saw a team perform what they call an “acoustic side-channel attack.” You know those folks that use specific G-Code to program their 3D printers to play Bach… or the Super Mario theme song? Well, this is sort of the opposite of that. Just as the printer’s toolpath can result in a symphony of sound, a symphony of sound can be reverse engineered back into its toolpath.
By applying a set of algorithms to a printer’s sounds as it’s printing an object, the team was able to determine the amount of power being supplied to its motors, the speed at which it was printing, and the torque applied. They tested their hypothesis by recording the sounds of a PrintrBot machine as it fabricated a simple object, specifically the outline of a key, and then translating their data back into a new 3D printed object, achieving almost 90% accuracy.
With improved algorithms, it’s possible that this accuracy could be pushed even further and the researchers believe that an app could be designed for use within smartphones. The key shape is an interesting object to have chosen for this study, as there have been numerous examples of key duplication performed with 3D printing. This could be extrapolated to IP from high-profile companies or possibly even military secrets. In order to prevent such 3D model theft, the study’s authors recommend sound dampening to prevent your printer from working as a double agent.