Within the digitized world of additive manufacturing, the storage and transfer of huge streams of sensitive data have become commonplace. Data includes individual SMEs passing technical IP documents between departments, but it also includes entire distributed manufacturing networks, for example transferring aerospace part files from one country to another.
I sat down with Nikhil Gupta, a professor at New York University’s Tandon School of Engineering, and Jing Zhang, a professor of engineering at Purdue University Indianapolis, to better understand the current state of 3D printing cybersecurity, the main risks, and what we could be doing as an industry to secure our 3D printing data.
With the ongoing industrialization of 3D printing, both 3D printers and manufacturing facilities are becoming increasingly IoT-connected. As convenient as this is, it gives rise to the threat of cybersecurity breaches, and 3D printing technology is well on its way to outpacing the competency of its own security infrastructure.
In fact, according to this Deloitte study, up to 40% of advanced manufacturing firms had suffered a cybersecurity incident in the past year, owing to the implementation of cutting-edge production technologies. Of those affected, 38% had suffered damages in excess of $1 million.
Ralph Resnick, Founding Director of America Makes, also attributes the growing risk to increasing connectivity on the shop floor. And still, a recent America Makes survey revealed that only 37.7% of additive manufacturing organizations have conducted a formal or informal cyber risk assessment.
”There is a critical difference between industries like finance and industries like manufacturing when it comes to cybersecurity,” says Gupta, who co-authored Manufacturing and Security Challenges in 3D Printing. “Banks can change the stolen credit card numbers to stop future losses. However, part designs often aren’t changed for years, even decades. Hence, solutions specific to the manufacturing industry need to be developed.”
IP theft and process sabotage
According to Zhang, there are two main cybersecurity risks in 3D printing: IP theft and process sabotage. While these won’t apply to the average joe printing decorative pieces in the workshop, companies, research institutions, and state organizations handling any kind of sensitive 3D printing data should be wary.
The risk of IP theft is typically not an issue when considering in-house design and prototyping, as security vulnerabilities really begin to appear when outsourcing production to higher-volume manufacturing facilities. As well as 3D part files, companies should work to secure their process parameters too, seeing as many of these can take years to develop and fine-tune for industrial parts.
IP can be stolen in any number of ways. Cloud-based file-sharing systems may be hacked, email servers can be breached, and solid 3D printed parts may even be reverse-engineered using 3D scanning technology. If the end goal is to counterfeit a product, this may lead to major revenue losses for a company.
Zhang told 3D Printing Industry, “By using non-destructive testing techniques such as CT scanning, the internal microstructure of a printed part can also be revealed, which can be used to derive the used processing parameters.”
When it comes to process sabotage, the main risk is the malicious modification of part data, which can lead to increased in-service failure rates. Quality assurance and individual part testing can alleviate this risk, but these measures are both time and cost-intensive. This makes them unfeasible for high part volumes.
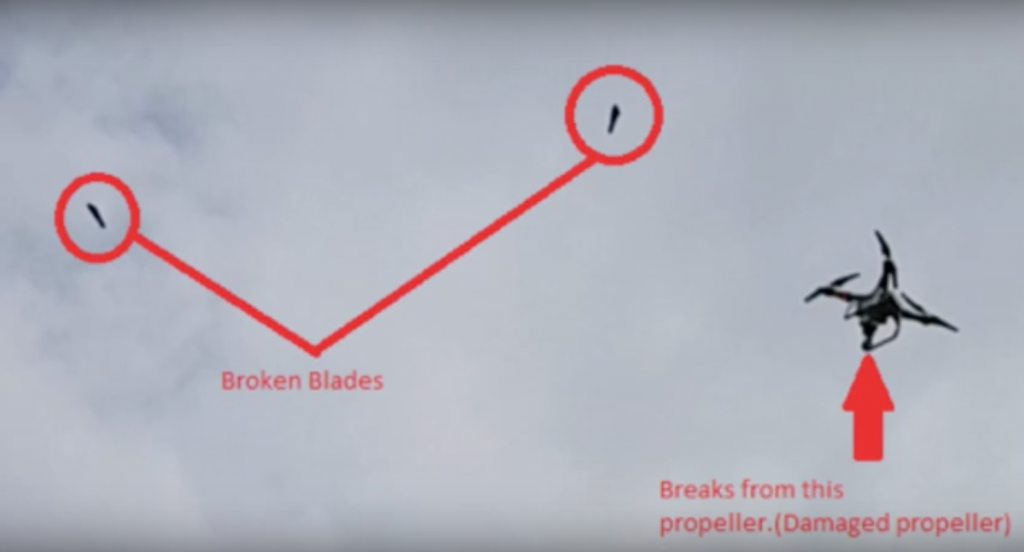
To demonstrate just how catastrophic process sabotage can be, researchers from Ben-Gurion University of the Negev, University of South Alabama, and Singapore University of Technology and Design have previously hacked into a 3D printer used to fabricate drone components. The team made undetectable modifications to the 3D printed propellers of the drone, which were visually discrete enough to make it past quality assurance. However, after just two minutes of flight time the propeller snapped, downing the drone seemingly out of nowhere.
Zhang adds, “The STL and toolpath files can be modified by introducing internal features without affecting the exterior appearance. This can compromise the integrity and properties of the printed parts.”
What measures do we currently have in place?
Many of the measures the 3D printing industry currently has in place are not all that different from more general cybersecurity techniques. Organizations employ firewalls to prevent access to sensitive databases and encrypt their 3D files to alleviate the risk of interception. One cybersecurity technology cannot protect against every threat, however, and there are now a number of more 3D printing-centric technologies being developed.
A patent recently issued to Gupta’s NYU team describes how security features can be programmed right into the design of a CAD file itself. By splitting a model up into at least two parts, the sections can be digitally displaced to make them impossible to print without knowing the offset. The clever approach is just one way of preventing part counterfeiting, almost like a digital watermark that renders a stolen model useless.
Elsewhere, blockchain as a service (BaaS) company SIMBA Chain has previously collaborated with the US Air Force to help secure defense supply chains using smart contracts. By registering and tracking supply chain data on an immutable blockchain ledger, sensitive information such as part files can be sent to forward forces free from unwanted surveillance. This ensures on-demand equipment repairs cannot be interfered with on the front lines.
When it comes to combating process sabotage, Dr. Jeremy Straub, a computer science professor at North Dakota State University, has previously proposed an intelligent vision-based part monitoring system. The monitoring process would work in real-time alongside a 3D printer, using an array of five cameras to compare the printed part to the expected shape of the reference STL file. As such, it would be able to detect visual cues that could suggest a defective print, enabling users to abort faulty prints without requiring any part testing.

The next steps for the 3D printing industry
It’s not all doom and gloom, as there is a route to security in all of this by way of improved education and greater investments. While the technology readiness of the individual measures is largely there, it is our ability to apply our tools that is lacking.
Gupta says, “More investment is required, but the critical need is to develop training programs where manufacturing and cybersecurity professionals interact with each other and understand each other’s needs and limitations.”
NYU is currently working on one such program, whereby it will provide graduate-level courses on additive manufacturing security. Backed by a grant from the National Science Foundation, the course will train mechanical engineering students in the principles of cybersecurity.
Zhang agrees with the sentiment on collaboration: “For companies, an interdisciplinary approach is required to fully understand and analyze the risks. The team should be composed of experts from mechanical engineering, electrical engineering, computer science, industrial engineering, and other disciplines. For the public, general education of the potential risks and receiving necessary training on mitigation are required.”
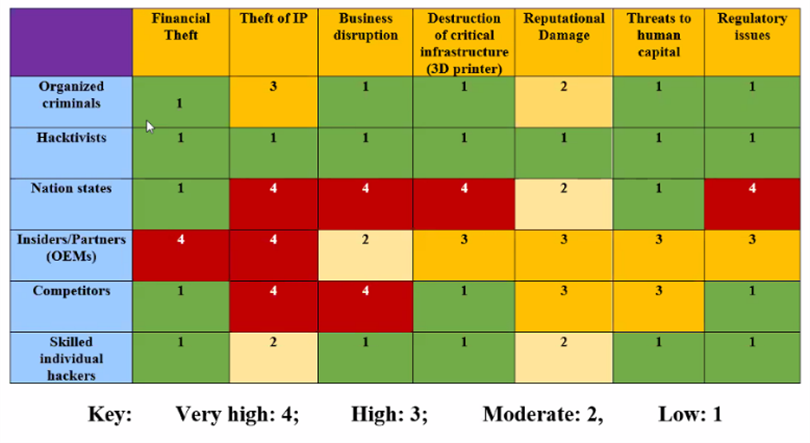
With interdisciplinary teams, companies would be better equipped to conduct comprehensive risk analyses. Heat maps are a common way of doing this, whereby possible resource investments are assessed for their potential impacts. As we’ve seen, there are several security approaches available but applying them all is often too costly, so carefully planned risk assessments can help with crucial resource allocation and decision making.
Ultimately, it comes down to two minds being better than one. As the complexity of 3D printing technology itself increases, so does the complexity of the cybersecurity risk, and the budding nature of the problem renders it difficult to solve. By tackling the issue in a collaborative manner, we can help ensure the additive manufacturing sector grows safely and securely.
Subscribe to the 3D Printing Industry newsletter for the latest news in additive manufacturing. You can also stay connected by following us on Twitter, liking us on Facebook, and tuning into the 3D Printing Industry YouTube Channel.
Looking for a career in additive manufacturing? Visit 3D Printing Jobs for a selection of roles in the industry.
Featured image shows an Arburg Freeformer 3D printing facility. Photo via Arburg.



