Two years ago, a few different stories popped up featuring disparate lock-pickers devising methods for copying keys with 3D printing. The practice grabbed so much attention that more than one startup even emerged as digital locksmiths that could store copies of your keys for the inevitable day when you’d drop your originals down a sewer drain or forget them in your car. Since then, the topic died down so that everyone could return to talking about 3D printed guns. Good news for fear-mongers! A new site has come alive that provides a CAD tool to copy keys. This time, the developers are bonafide uni researchers from the University of Michigan that have launched Keysforge as a means of proving that so-called high-security keys aren’t as secure as one might think.
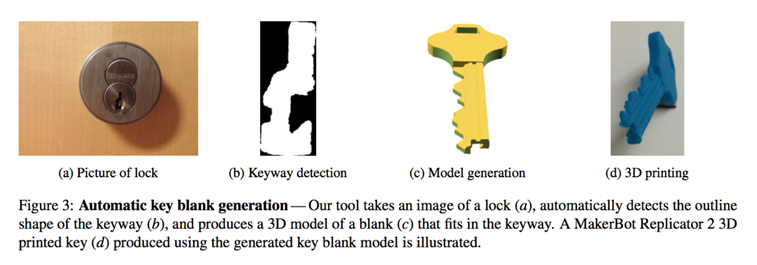
While lockmakers like Schlage will create high security keys with complex shapes, called keyways, to prevent copying, Keysforge allows anyone to convert a photo of the front of the lock into a CAD file for 3D printing. Any lock system that relies on standard A-2 pin placing can be decoded, as long as you know how many depth cuts the key has and a front facing photo of the lock you want to pick. Researcher Ben Burgess tells Wired, “We’ve proven that restricted keyways are no longer a defense. We’ve shown that anyone with a 3-D printer can quickly and easily attack these systems.”
Best of all, the researchers have made Keysforge public to showcase just how disruptive 3D printing might be to secure lockmakers. They also discovered that ordinary PLA could be perfect for temporary key copies, finding it to work better than nylon. They also learned that 3D printed stainless steel, while strong, might damage the lock, ultimately determining 3D printed brass to work the best. This means that it might be possible to order a key copy via 3D printing service providers or, if you’re looking for temp keys, at home on a desktop 3D printers.
You can let your imagine what one might do with these 3D printed forgeries. Wired points out that, not only could disgruntled employees use the software to do damage to a place of work, but it might even be possible to collect various keys and compile their shapes into a single master key to unlock every door in a given facility or building, as demonstrated by University of Pennsylvania computer scientist Matt Blaze. Burgess continues, “One of the biggest defenses for these methods was restricted keyways. This reopens those attacks.”
In the past, when key copying and 3D printing found themselves in bed together, a Shapeways representative stated that the company has not restricted the practice of key duplication, saying Shapeways “doesn’t have any specific policies around printing keys or lock picking tools, but it is up to our users to responsibly comply with our overall guidelines.” i.materialise, however, commented on a previous use of their services for key duplication, “i.materialise rejects any use of its services to promote activities or to create products which pose a safety or security risk to others. Had the intentions of David Lawrence and Eric Van Albert been known to i.materialise, the key would not have been printed.”
Wired reached out to lockmakers about the Keysforge project, with only Medeco responding. Medeco spokesperson Clyde Roberson said that the work was “important and informative.”, before saying, “Medeco and [its parent company] ASSA ABLOY have been researching this topic and have been actively pursuing improvements in our technology to help minimize this threat. This includes testing various scanning and printing devices available on the market, from highest quality to lowest. We have already developed some products directly as a result of this work and future products will continue to reflect added protection for this threat.”
Eric Wustrow, another researcher on the project, told Wired that the study should provide a lesson to lockmakers, “Attackers and criminals, especially the high end ones, will learn these attacks. If this is a world where only the manufactures and the attackers know what’s going on, it’s dishonest to sell these [restricted keys] to consumers.” He added, “This lets consumers know what they’re buying—that restricted keyways won’t necessarily give them the best defense. And it shows lock manufacturers that they need to improve their designs.”
To overcome this potential threat, the researchers indicate that those relying on high-security locks should switch to electronic systems. Of course, there may be methods for hacking those electronically, as we’ve learned from TV and movies. And it may not be the big banks that have to worry about 3D printed keys, but small businesses that may not be able to afford the switch. Without being too preachy, my own solution involves a more equitable society to dis-incentivize people from theft and the promotion of empathy worldwide to discourage mean-spirited attacks. The Michigan researchers plan to present their study at the Usenix Workshop on Offensive Technologies, but, before then, I’ll bet that this study gets a lot of attention. And, before they can take Keysforge down, I’m sure plenty of people will be able to get the code from GitHub to make their own Keysforge copies.