Voting shortlists for the 2021 3D Printing Industry Awards are now open. Who do you think should receive top honors this year? Have your say now.
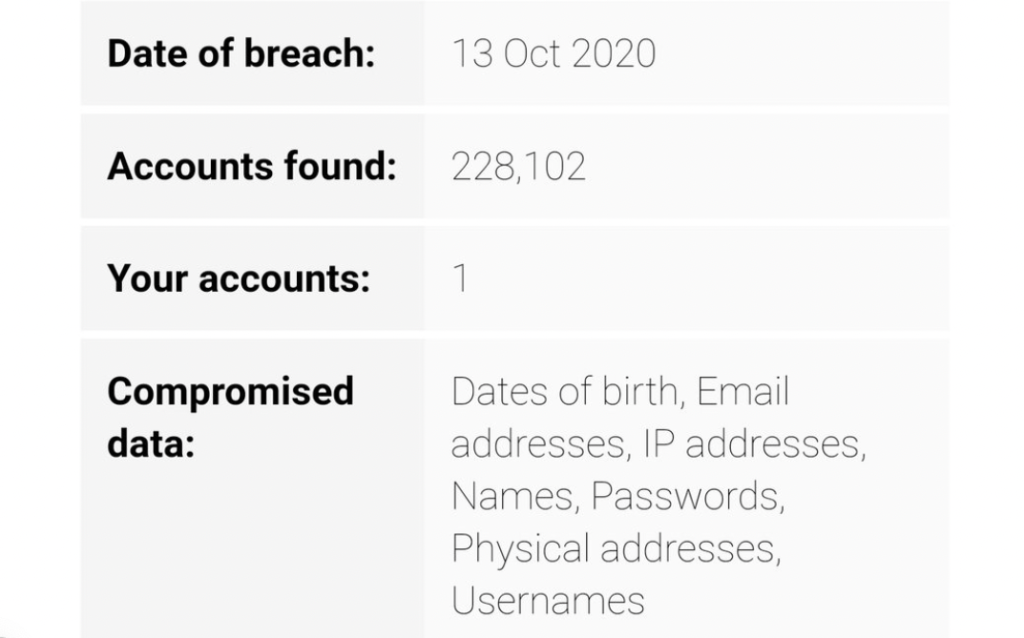
Digital 3D model repository Thingiverse has suffered a mass data breach in which the personal information of around 228,000 subscribers has been made publicly available online.
Initially leaked in October 2020, the 36 gigabyte data cache is said to contain unique email addresses and other information that could be exploited as a means of identifying users. While these details have been circulating online for over a year, data breach notification service provider ‘Have I Been Pwned’ has now found evidence that it is “extensively circulating within the hacking community.”
3D Printing Industry has reached out to Thingiverse for comment, but as of publication has yet to receive a response, and although the firm has told Have I been Pwned that it is “taking this matter very seriously,” at time of writing, Thingiverse has failed to notify affected users. [see update at end of article]
MakerBot’s open model platform
Founded by MakerBot back in 2008, Thingiverse is a self-styled hub for the maker community, where they can freely post the files needed for others to 3D print their model designs. As of October 2018, the platform had racked up more than two million registered users as well as facilitating over 340 million object downloads, and it has continued to grow in scope and popularity in the three years since.
In addition to providing users with access to at least 1.6 million different designs, the site allows them to personalize models via its Customizer tool, or even use OpenSCAD to build their own from scratch. The platform also allows models to be uploaded under the GNU General Public or Creative Commons licenses, thus it has become popular with those creatives seeking to share and discuss their work.
However, Thingiverse’s open nature has previously made it vulnerable to hacks, and in December 2017, a flaw within the site’s comment section allowed hackers to use it as a means of mining cryptocurrencies. In effect, this vulnerability enabled the perpetrators to harness the CPU power of visitors’ computers, and redeploy it to perform the calculations needed to mine for digital currencies such as Bitcoin.
At the time, MakerBot stated that the security flaws behind the hack had been rectified, so “Thingiverse users don’t need to worry about people hijacking their things, nor do they need to take extra measures to protect their computers.” The firm added that it had banned offenders, while “mining scripts never had access to users’ private data,” but in its latest hack, this doesn’t appear to be the case.
Thingihack II: this time it’s personal
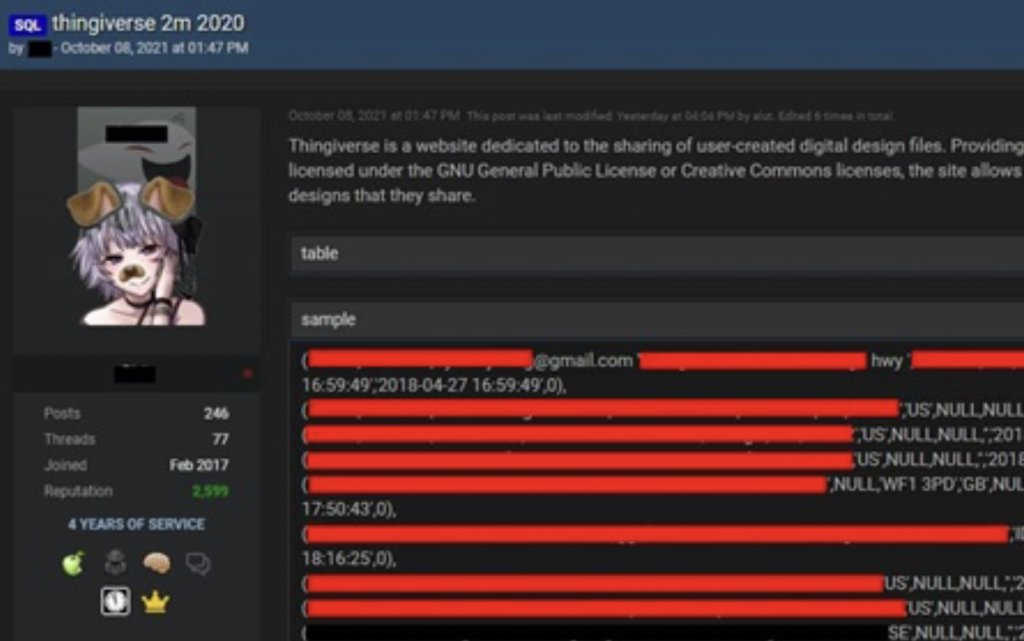
Thingiverse’s latest leak has been publicized by ‘Have I Been Pwned’ creator Troy Hunt, who was alerted to the compromised data on a popular hacking forum. Since then, he has tried to pick through the details, reportedly telling cybersecurity intelligence firm Information Security Media Group (ISMG) that it includes more than 255 million lines of data.
“The earliest date stamps in the data set appear to go back about a decade, however, I’ve not analyzed it closely enough,” Hunt told ISMG. “There is data on the 3D models that are publicly accessible, but there are also email and IP addresses, usernames, physical addresses and full names.”
According to Have I Been Pwned’s website, the data cache itself originated in a leaked Thingiverse backup, with email addresses mostly coming from comments left on 3D models. While these emails are understood to have been shared in the webdev+ format (e.g. [username]@makerbot.com), users’ names, addresses and passwords are included as crypto-friendly unsalted SHA-1 or bcrypt hash files.
Worryingly, through his own investigation into the data, Hunt has found that the presence of bcrypt password hashes in the data could indicate users’ dates of birth, but more promisingly, he still hasn’t identified any ‘plain text’ password exposure.
What next for Thingiverse?
Hunt was first alerted to Thingiverse’s data leak by ‘pompompurin,’ a cyber aficionado with a presence on Twitter as well as forums such as Keybase. Having found the information cache on October 1 2021, they initially verified its validity by sharing it with a fellow enthusiast, before identifying its cause as having likely been a ‘misconfigured S3 bucket,’ and contacting MakerBot directly with their concerns.
Frustrated by a perceived lack of action from MakerBot, pompompurin’s cyberfriend posted the data on a known hacker forum, justifying the move by saying that “they deserve that to happen after being so reckless as to leaving a backup public.”
Much like pompompurin, 3D Printing Industry, the ISMG and Hunt have all reached out to MakerBot for comment on the data leak, but thus far it has failed to respond. Elsewhere, Hunt has made his own appeal to Thingiverse on Twitter, asking for the personal contact details of the site’s security team, saying that he “uses the site a lot himself so he’d *really* like to get in touch with someone there.”
Although his tweet hasn’t gained a great deal of traction so far, Twitter user ‘Rapterron’ has responded by criticizing Thingiverse for being “the most neglected and still-used platform he’d ever seen,” and quipped that it’s “time to change the passwords, and move to Prusa.”
UPDATE: 22:00 BST, 14/10/21
A spokesperson for Makerbot has provided the following comment, “We became aware of and have addressed an internal human error that led to the exposure of some non-sensitive user data for a handful of Thingverse users. We have not identified any suspicious attempts to access Thingiverse accounts, and we encouraged the relevant Thingiverse members to update their passwords as a precautionary measure. We apologize for this incident and regret any inconvenience it has caused users. We are committed to protecting our valued stakeholders and assets, through transparency and rigorous security management.”
To stay up to date with the latest 3D printing news, don’t forget to subscribe to the 3D Printing Industry newsletter or follow us on Twitter or liking our page on Facebook.
For a deeper dive into additive manufacturing, you can now subscribe to our Youtube channel, featuring discussion, debriefs, and shots of 3D printing in-action.
Are you looking for a job in the additive manufacturing industry? Visit 3D Printing Jobs for a selection of roles in the industry.
Featured image shows a 3D printable ‘hacked’ stamp developed by Thingiverse maker ‘Clocktimer.’ Photo via Clocktimer.