A paper has been released supporting the claims that a team of researchers from Ben-Gurion University of the Negev (BGU), the University of South Alabama, and Singapore University of Technology and Design have managed to hack into a system used to 3D print drone components.
The purpose of the project
The abstract of the paper, titled drOwned – Cyber-Physical Attack with Additive Manufacturing (drOwned: drone and owned) states that the experiment was conducted due to concerns raised by [Additive Manufacturing’s] dependence on computerization. In order to emphasize their point, researchers needed to prove how easy it would be to execute such a hack, and also conduct modifications accurate enough to go unnoticed in a finished printed product, yet also allow a completed drone to break once already in-flight.
How they did it
With the driving force of a drone being in the propellers, this segment became the obvious choice for a malicious interception. The question then was how exactly to go about it. Intersection started at the joint where two blades meet a centralized ‘cap’. See below for a diagram to explain:
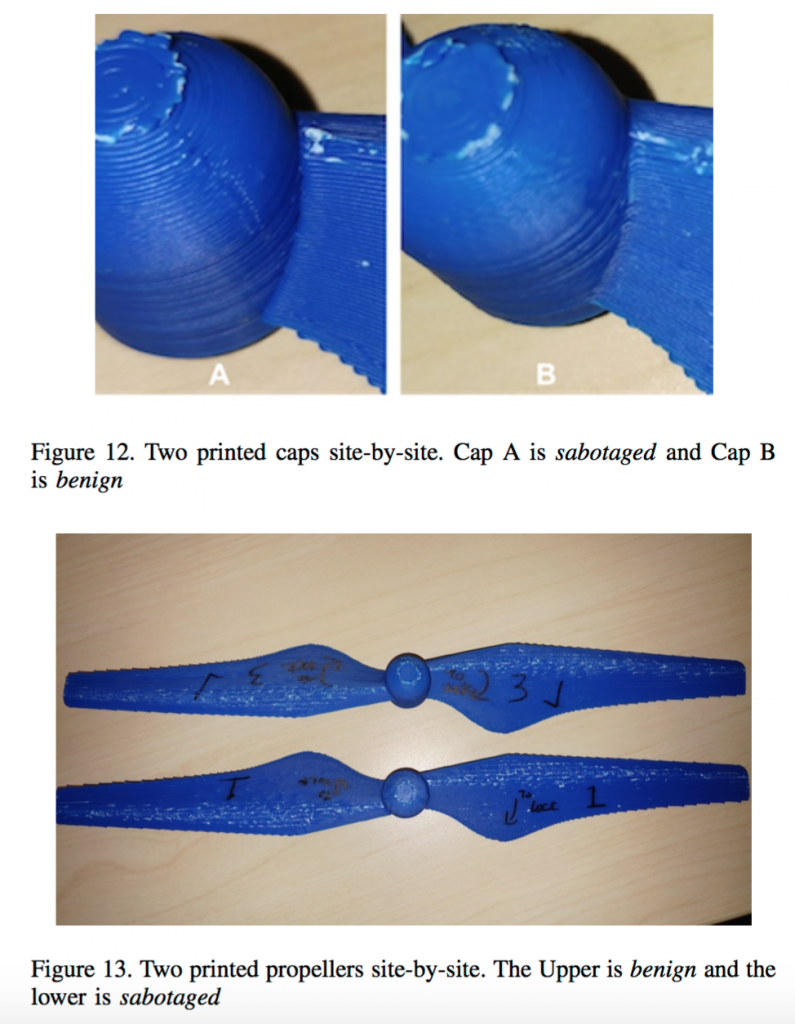
‘even with a basic physics knowledge it is obvious that the biggest force is applied at the joint connecting the blades and the cap of the propeller together. Therefore, this joint appears to be a good location to insert a defect in the design. Furthermore, if propeller breaks at this joint, the loss of thrust will be the maximal compared to all other places where a defect can be introduced.’
Above: An extract from ‘6.3.1. Location of Defect’ section of the journal.
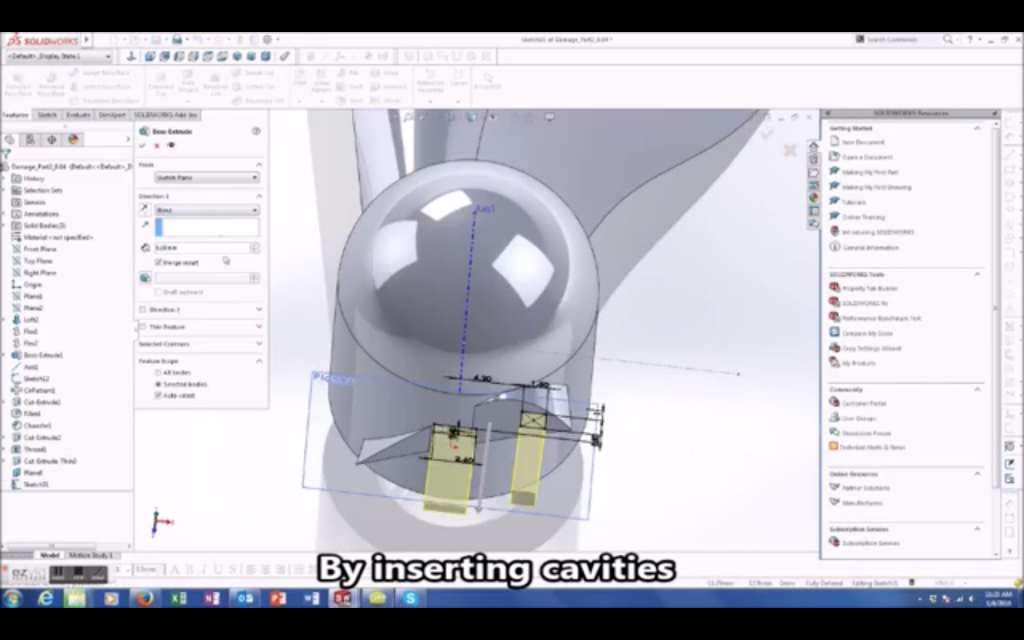
After this was decided, the team then started by physically drilling holes between the blades and the cap, but found that circular holes in fact contributed to the ‘stress distribution’ of a part. This meant that the defective propeller would be noticed as it moved more slowly than it was supposed to. Consequently, the end design took on the shape of rectangular shaped cavities that were then inserted into the 3D model of the propeller.
The cyber attack
After finding a structure that worked, the team tested their safety concerns through a simple phishing scam. Once files from the email were downloaded, the researchers could easily access the 3D propeller models and make their changes, as seen in their video which can be found on Youtube.
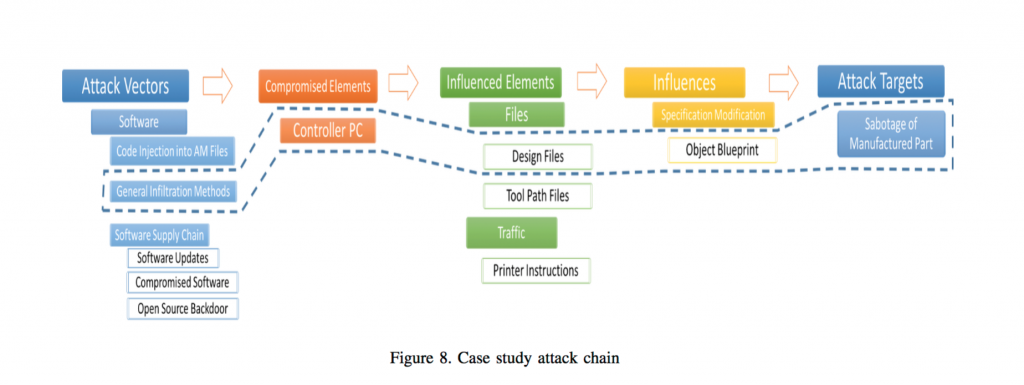
While the means of access to a subject’s computer maybe be considered crude by some, (I was here thinking ‘but who would download a zip file from an unknown source?’) it is instead the implications of what they have done that speak volumes on the security surrounding 3D printing as a manufacturing method of secure objects. In this, drOwned successfully makes its case; ‘in order to protect public safety and national security, solutions should be found and implemented that will increase both robustness and resilience of AM to sabotage attacks.’
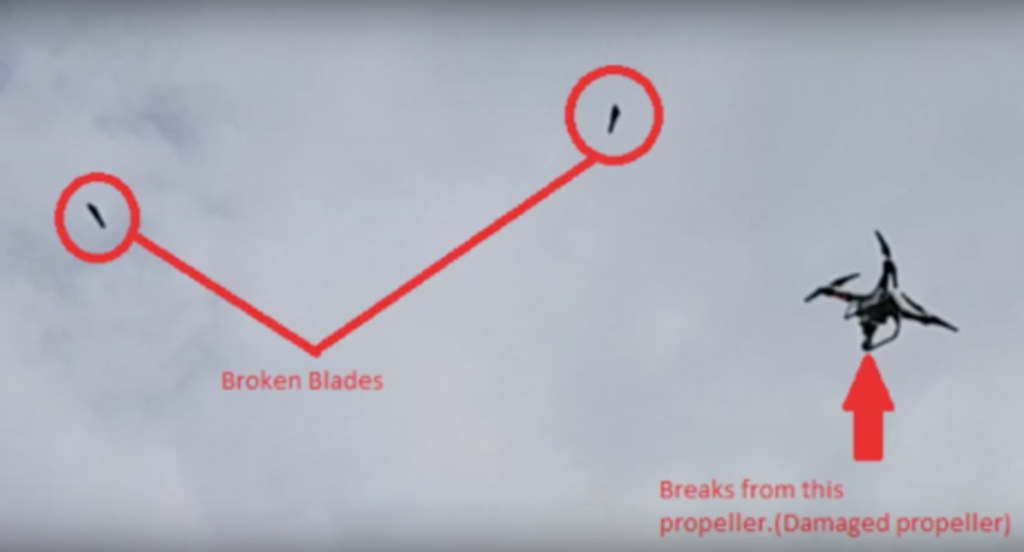
Featured image: Quadcopter with one defective propeller out of four. Image via: Yuval Elovici


