Three MIT electrical engineering students have used 3D printing to get around the pesky “Do Not Duplicate” label engraved on the keys to your apartment, and to high-security locks everywhere. David Lawrence[1], Eric Van Albert, and Robert Johnson announced that, at last weekend’s DefCon hacker conference, they would release some code that anyone can use to reproduce the key for any high-security Primus locks manufactured by the Schlage lock making company.
Lawrence, Van Albert and Johnson were able to scan the keys to Primus locks using a flatbed scanner and generate a 3D model, which they then created nylon copies of via Shapeways. Of course, you can get your personal non-duplicable keys copied at most local hardware stores, if you cover up the words “Do Not Duplicate” with electrical tape, as Tony C. points out on Yelp. But for the Primus locks that educational facilities, hospitals, government buildings, and prisons might use, one has to go directly through Schlage to get a copy. Forbes’ Andy Greenberg writes that famous lock picking specialist, Marc Weber Tobias, has said that he uses Primus locks for his own professional and personal use. With the code generated by these hackers, however, it’s possible to 3D print a copy simply from a photograph of the key.
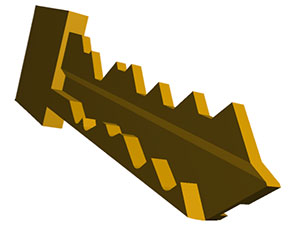
Because Lawrence, Van Albert and Johnson have deciphered the two sets of metal teeth that line the surface of Schlage Primus keys, they can create a 3D model using their code, which can be 3D printed in a range of materials, including titanium, by a company like i.materialise. All they need is a photo of the key that needs to be duplicated. David Lawrence tells Forbes that “All you need is a friend that works there, or to take a picture of their key, or even a picture of the key hanging off their belt. Pirating keys is becoming like pirating movies. Someone still has to get the information in the first place, but then everyone can get a copy.”
i.materialise has already commented on the story, saying, “i.materialise rejects any use of its services to promote activities or to create products which pose a safety or security risk to others. Had the intentions of David Lawrence and Eric Van Albert been known to i.materialise, the key would not have been printed.”

Security is like a Chinese finger trap. The more you try to break free, the tighter it becomes. And what these hackers have done is given us the illusion of freedom, while making the trap tighter. By rendering mechanical locks obsolete, we have become more deeply entrenched in the high-tech security state. Of course, if it wasn’t these individuals, it would have been someone else, as new technology causes us to do away with the old. The future will see us rely more and more heavily on electronic security systems and cryptography that will, in turn, cause hackers to develop new methods of circumvention, which will lead to new security measures and so on and so on until we learn to gently press our fingers together and remove the trap entirely.
Source: Forbes
[1] Not to be confused with the David Lawrence I went to college with.


